This is an old revision of the document!
Table of Contents
OpenCL BitLocker
BitLocker is a full-disk encryption feature available in recent Windows versions (Vista, 7, 8.1 and 10) Pro and Enterprise.
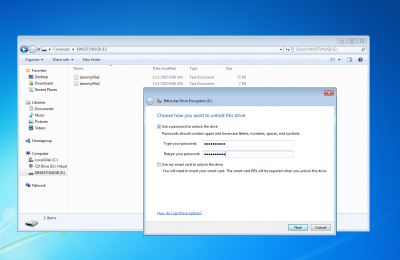
BitLocker-OpenCL format attacks memory units encrypted with the password authentication mode of BitLocker (see the following picture).
Our attack has been tested on several memory devices encrypted with BitLocker on Windows 7, 8.1 and 10 (both compatible and not compatible mode).
You can find the standalone CUDA implementation here: https://github.com/e-ago/bitcracker
How To
In order to use the BitLocker-OpenCL format, you must produce a well-formatted hash of your encrypted image. Samples BitLocker images for testing are available at https://github.com/kholia/libbde/tree/bitlocker2john/samples and here: https://github.com/e-ago/bitcracker/tree/master/Images
Method 1
Use the bitlocker2john tool (john repo) to extract the hash from the password protected BitLocker encrypted volumes.
$ ../run/bitlocker2john minimalistic.raw Signature found at 0x00010003 Version: 8 Invalid version, looking for a signature with valid version... Signature found at 0x02110000 Version: 2 (Windows 7 or later) VMK entry found at 0x021100b6 Key protector with user password found minimalistic.raw:$bitlocker$0$16$e221443f32c419b74504ed51b0d66dbf$1048576$12$704e12c6c319d00103000000$60$000000000000000000000000000000002d135e69646c157c15b4c273ad85b86513a1672ae3f531ce121889178c669d37f8e5e0100d331ce78484844c
Method 2
First, build the “bitlocker2john” (external repo: https://github.com/kholia/bitlocker2john) project from source. See https://github.com/libyal/libbde/wiki/Building for help. Second, use the built bitlocker2john project to extract hash(es) from the encrypted BitLocker volume.
$ fdisk -l bitlocker-1.raw Disk bitlocker-1.raw: 256 MiB, 268435456 bytes, 524288 sectors Units: sectors of 1 * 512 = 512 bytes Sector size (logical/physical): 512 bytes / 512 bytes I/O size (minimum/optimal): 512 bytes / 512 bytes Disklabel type: dos Disk identifier: 0xfd0b8218 Device Boot Start End Sectors Size Id Type bitlocker-1.raw1 128 518271 518144 253M 7 HPFS/NTFS/exFAT 128 (Start) * 512 (Sector size) => 65536 => volume offset $ ./bdetools/bdeinfo -o 65536 bitlocker-1.raw -p dummy bdeinfo 20170204 $bitlocker$0$16$73926f843bbb41ea2a89a28b114a1a24$1048576$12$30a81ef90c9dd20103000000$60$942f852f2dc4ba8a589f35e750f33a5838d3bdc1ed77893e02ae1ac866f396f8635301f36010e0fcef0949078338f549ddb70e15c9a598e80c905baa
For more help with bitlocker2john, see the following URLs,
https://github.com/libyal/libbde/wiki https://github.com/libyal/libbde/wiki/Troubleshooting
Cracking Process
Use the BitLocker-OpenCL format specifying the previous hash:
./john --format=bitlocker-opencl --wordlist=wordlist target_hash
Currently, this format is able to evaluate passwords having length between 8 (minimum password length) and 27 characters (implementation reasons). We will increase the max passwords size in the next release.
Output
An output example is:
./john --format=bitlocker-opencl --wordlist=wordlist hash Device 0: Tesla K80 Using default input encoding: UTF-8 Loaded 1 password hash (bitlocker-opencl [SHA-256 AES OpenCL]) Note: minimum length forced to 8 Press 'q' or Ctrl-C to abort, almost any other key for status password@123 (?)
This OpenCL implementation has been tested on a GPU GeForce Titan X (Openwall), GPU AMD Radeon HD 7990 Malta and an Intel Core i7 Kaby Lake CPU.
References, license and contacts
BitCracker OpenCL version developed by Elenago <elena dot ago at gmail dot com> in 2015
Copyright © 2015-2017 Elenago and Massimo Bernaschi (National Research Council of Italy), <massimo dot bernaschi at gmail dot com>
Licensed under GPLv2
You can find the standalone CUDA implementation here: https://github.com/e-ago/bitcracker
This is a research project; for any additional info or to report any bug please contact <elena dot ago at gmail dot com>